Banner Security
There's a security problem with Banner. It's not huge, and the system does have safeguards against it, but they aren't tailored to the problem. The problem comes about with "Request an Unofficial Transcript - PDF version". The web version is fine: you need to be logged in to access that. The PDF version, however, sends a copy to your email. Seems okay, right? Wrong.
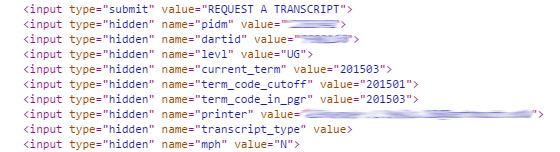
The problem arises when you look at the form that this button submits:
I blurred out my information, but it turns out most of it doesn't matter. The server automatically populates this form with hidden values when you load the page from the SQL database. There are a bunch of values such as what year you are, and when you want the Transcript to cover (those actually aren't updated at the right times: trying to download your transcript soon after grades are released will exclude the last term). Those don't matter. The three important values to focus on are "pidm", "dartid", and "printer". "pidm" is how Banner remembers who you are. It's linked to everything about you, and it's your Banner-specific identifier. "dartid" is your standard Dartmouth ID on your card, that you use to log in to everything: F0_____. "printer" is the email on your account.
Now one would imagine that this information maybe doesn't do anything. After all, it clearly HAS your email because it filled in the field. It should just send it to the email it has on file. However, IT DOESN'T DO THIS. It instead will send the transcript to whatever email you put there. Okay...that's a little weird. But it's probably okay. You'd have to know the "pidm" and the matching "dartid", and why would anyone ever know that.
Wrong again. See, you'd think that it would check that the "pidm" and "dartid" matched up with each other before sending it off to god knows what email address. But it doesn't. It doesn't even care what "dartid" is! So there's another field that's just useless. Alright, you say. So what: it shouldn't send unless you're logged into YOUR Banner account. Again, a good thought but wrong. If you have the "pidm" for any account, you can get it sent to your email if you simply log in as anyone.
Okay, you weakly argue. Who's gonna ever know my "pidm"?? It's a seven digit number (8 if it was filled up), and I didn't even know what it was. Well, the thing is, no one needs to know your "pidm". All they need is to run a quick python script that logs in and brute forces tons of them. With a seven digit number, you can run through every "pidm" in about 6 days of straight running. Then all you need to do is look at the PDF's...but that would take ages! Because the system automatically generates them, and EVEN IF THE PIDM IS INVALID IT DOES THIS. So there would be a ton of empty PDF's. Well, that's easily accounted for, by simply sorting by size and looking at the PDF's over the base "empty" size.
This is a pretty big problem. Now, it takes a while for the mail system to handle such a large brute force. But the simple fact is, the mail system shouldn't even be TRYING. It shouldn't be sending out transcripts, and it shouldn't send if there's an invalid "pidm". It shouldn't send to any email, and it should check you're logged in. And the "pidm" should be a 36 character hexadecimal string so that it's impossible to bruteforce. Unfortunately, none of this is currently in place, and there's nothing YOU, the average person can do about it. Except hope you have a large number.
This has since been fixed (by Dartmouth). The exploit may remain in any other school implementing older versions of Banner by Ellucian.