Roborock Routines and iOS Shortcuts
I have the Roborock S7 MaxV, and it's fantastic. It automates vacuuming and mopping, keeping my allergies under control at the touch of a button. I have a number of routines that I use, and wanted to schedule some of them to run. This is built into the app, but only allows you to do this for set times and days. I instead wanted to automatically suggest a full clean when I left the house (max once/day) where I could approve/disapprove, but was blocked by the poor integration between the iOS app and the normal way to do this kind of customized triggering, Shortcuts.
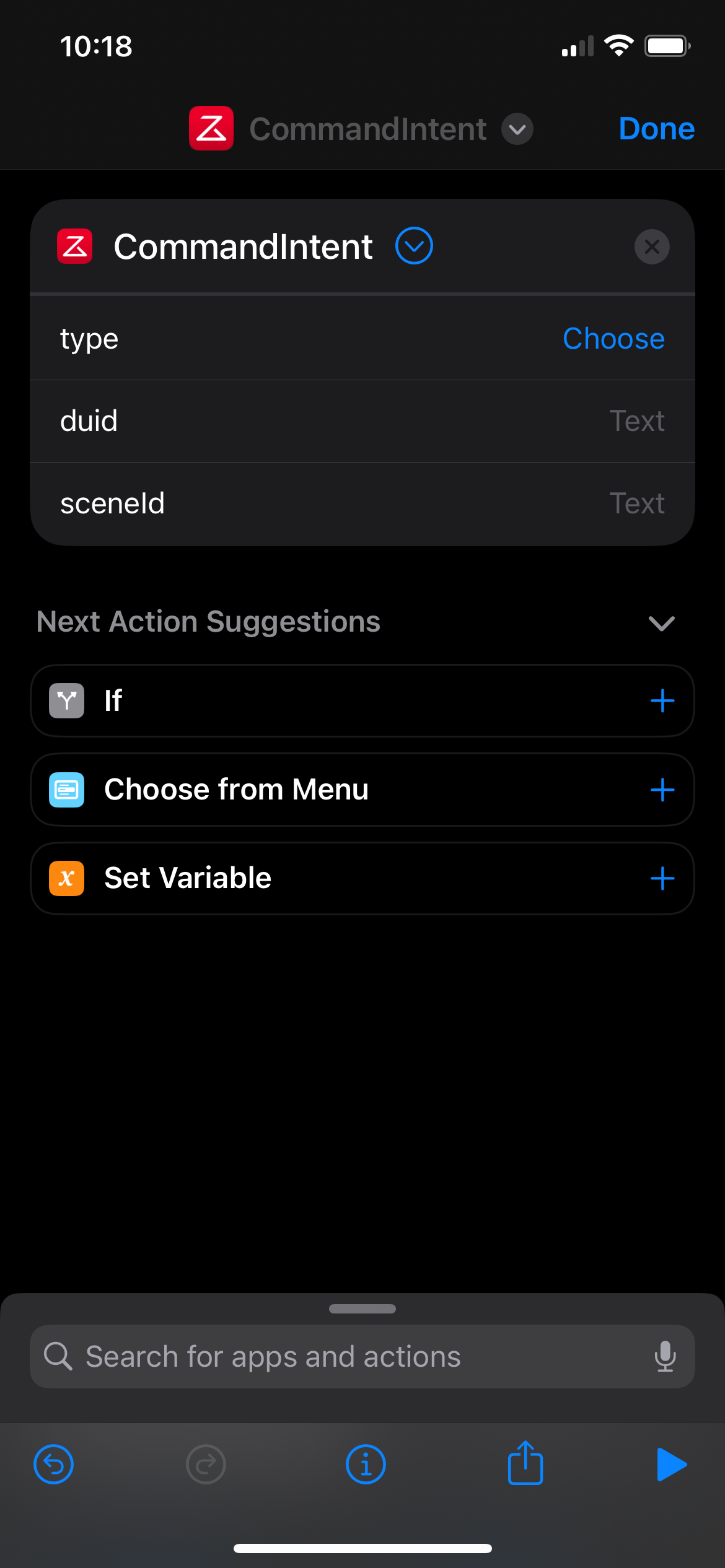
The only Shortcut that the app exposes is something called "CommandIntent", which while opaque felt like it could be used to trigger a routine if you had the type, duid, and sceneId.
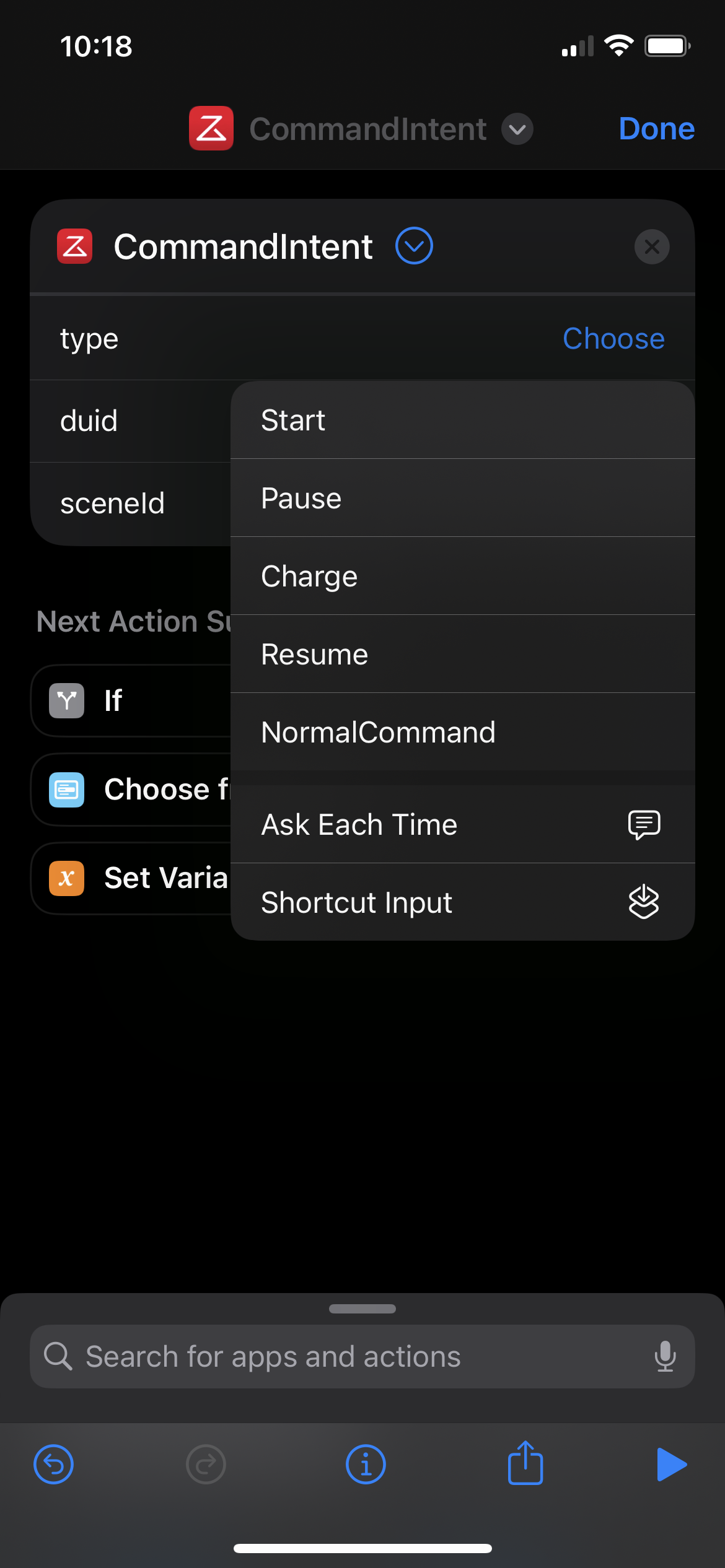
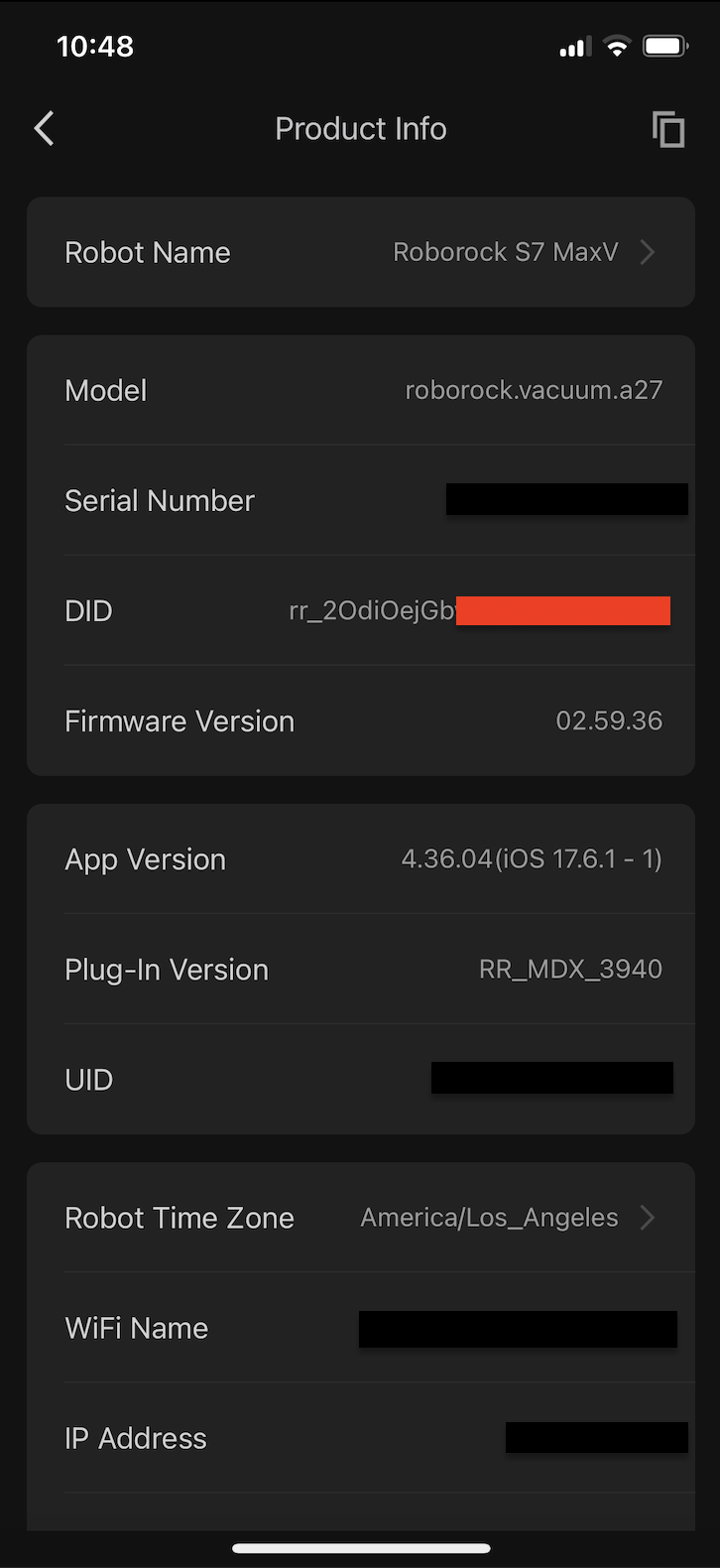
The type for triggering it is the helpfully named "NormalCommand". The duid is the Device ID, and can be obtained by clicking to the "Device" tab, "Enter" on your device, and then the triple dots in the top right to get to "Product Info". It's the DID field without the rr_ prefix, in this case 2OdiOejGb....
Unfortunately I couldn't find a good way in-app to find the scene IDs for the individual routines. Luckily Sashko Potapov just wrote up a writeup on how to do this in June. He used Charles Proxy, which needs a separate computer and a free trial, whereas I wanted a solution that could be done entirely on your phone. If you already have Charles set up then feel free to follow his instructions, but this is where my writeup will diverge to use an iOS app.
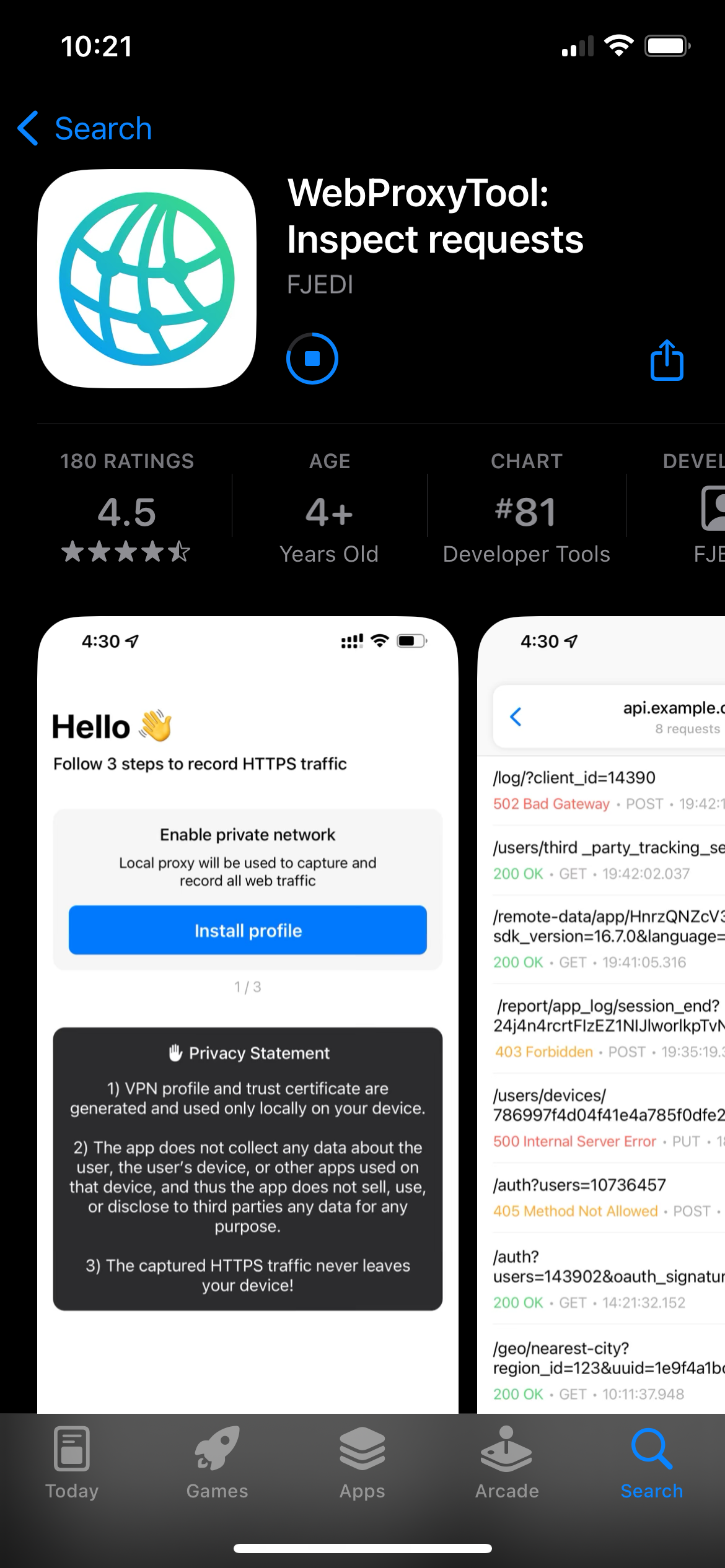
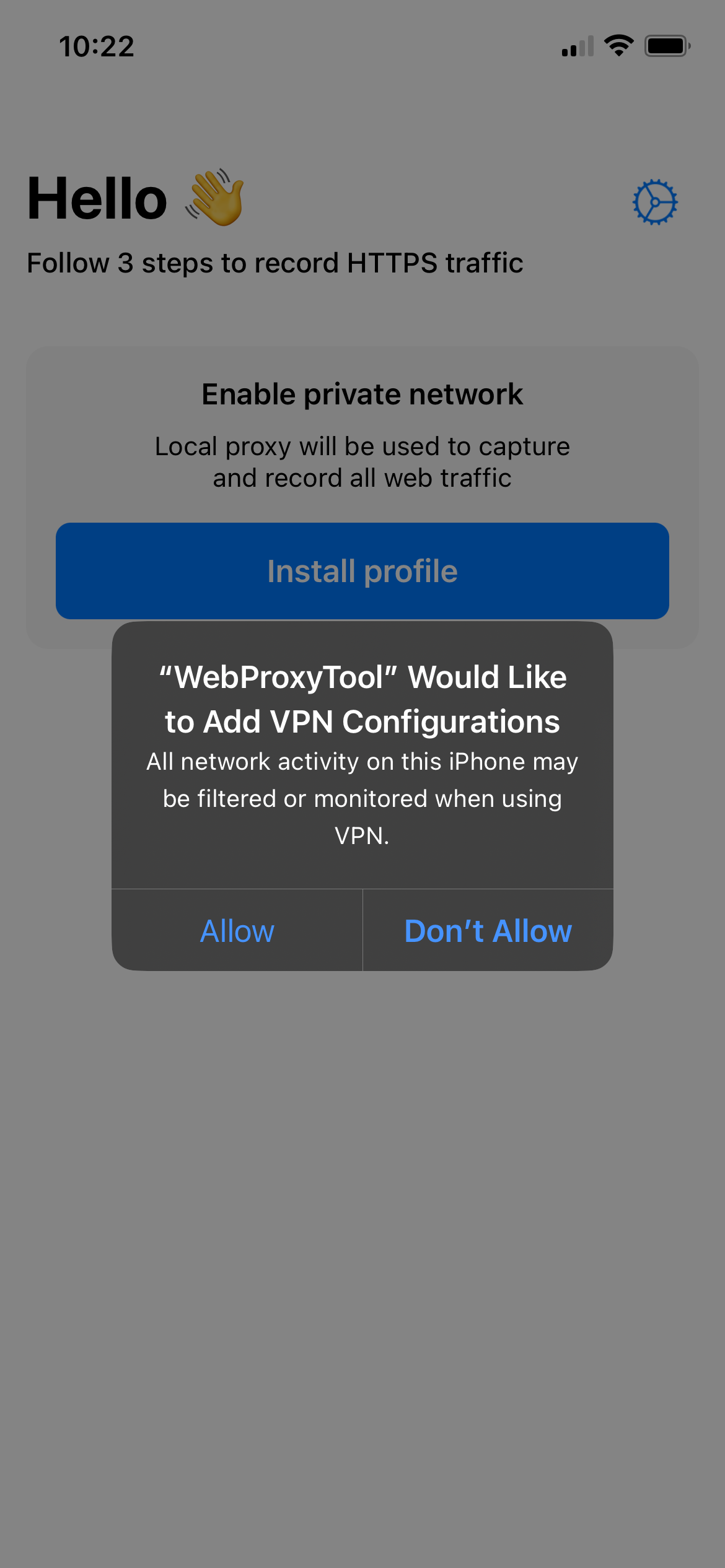
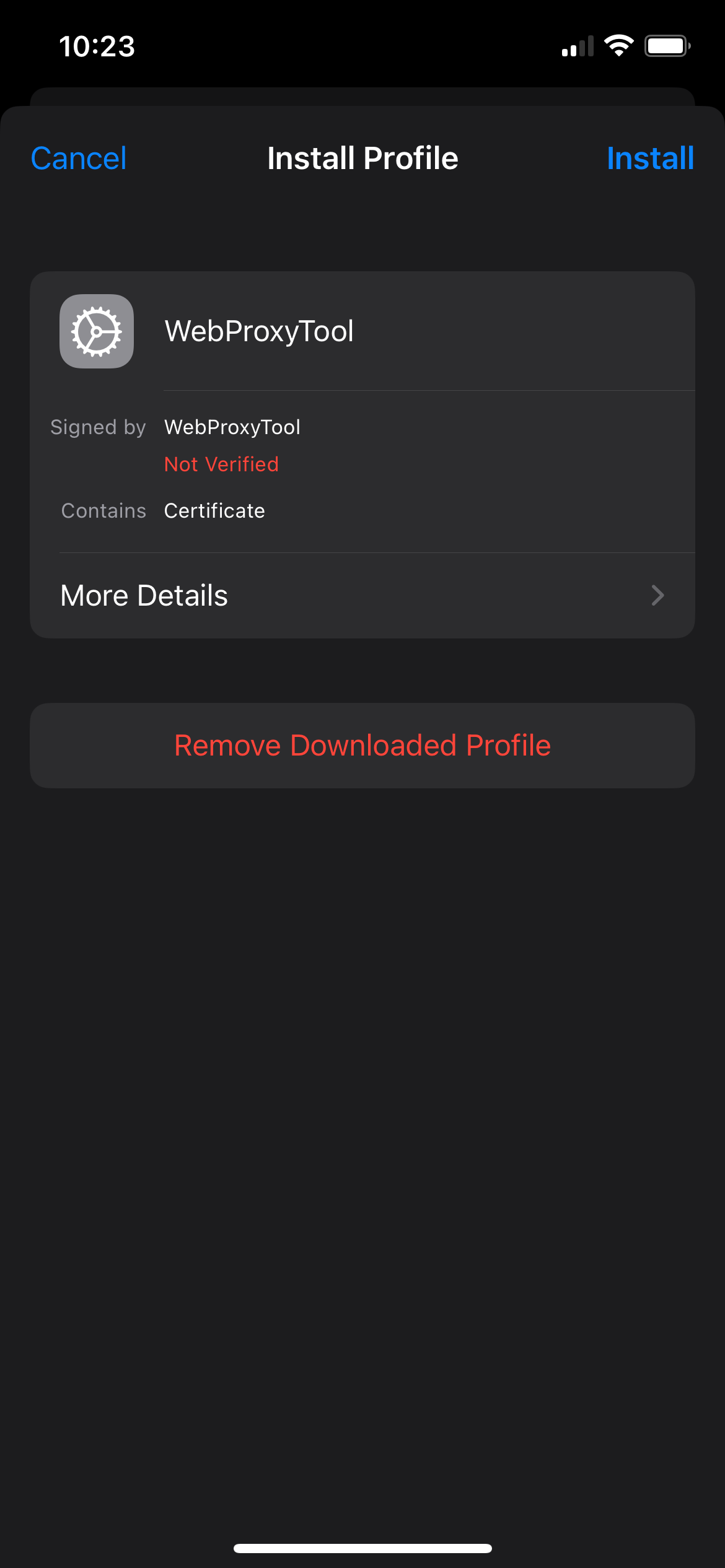
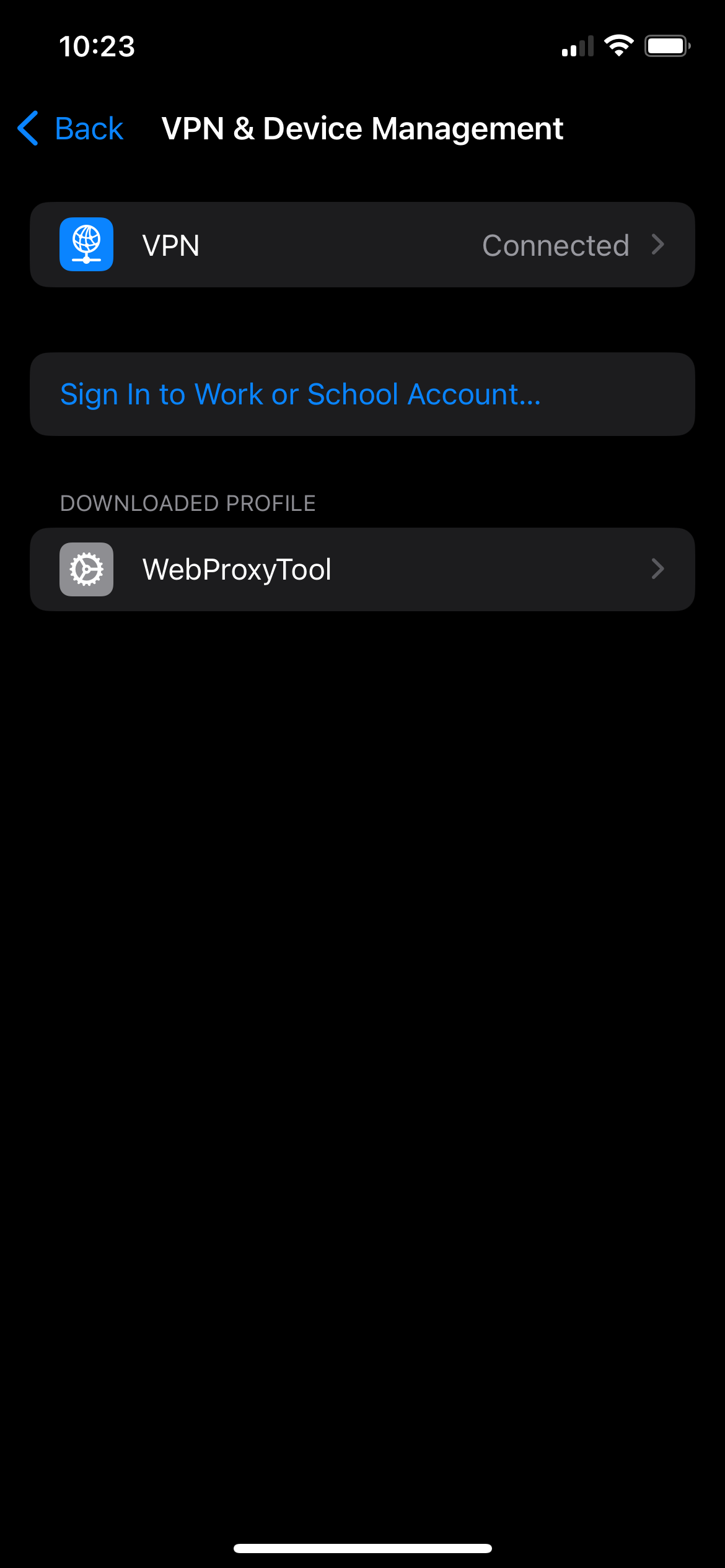
We'll instead be using WebProxyTool, a free 1 Since writing this the developer has added an $18/yr subscription. If it pops up asking you to subscribe you can just swipe the window down and ignore it. We don't need any of the paid features. iOS app. Follow the instructions from the app after you open it to install the VPN and trust the root certificate.
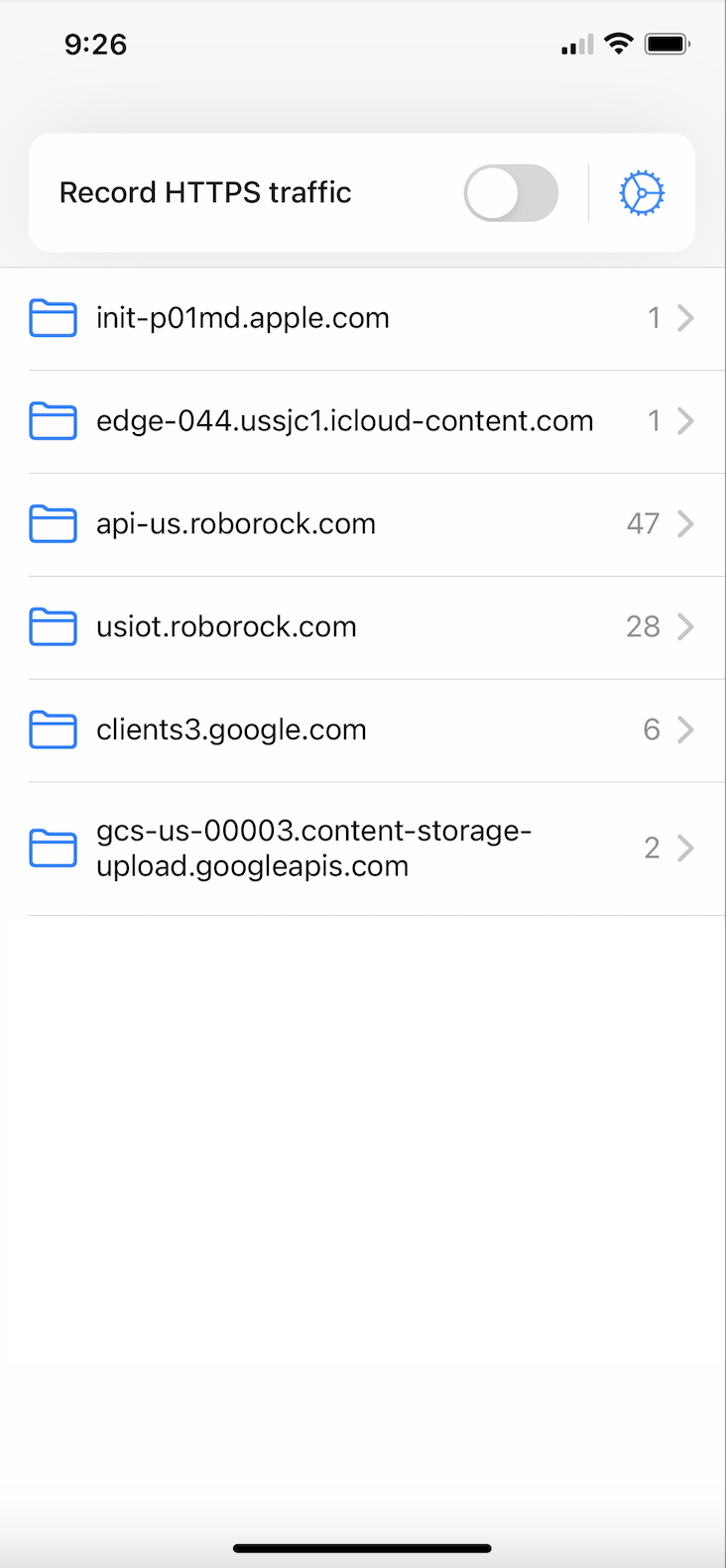
Then make sure "Record HTTPS Traffic"
2
In an update this was changed to "Enable WebProxyTool". In either case, this should be selected.
is checked at the top. By default HTTPS (or HTTP Secure) encrypts the data that is sent back and forth between servers so that your router/
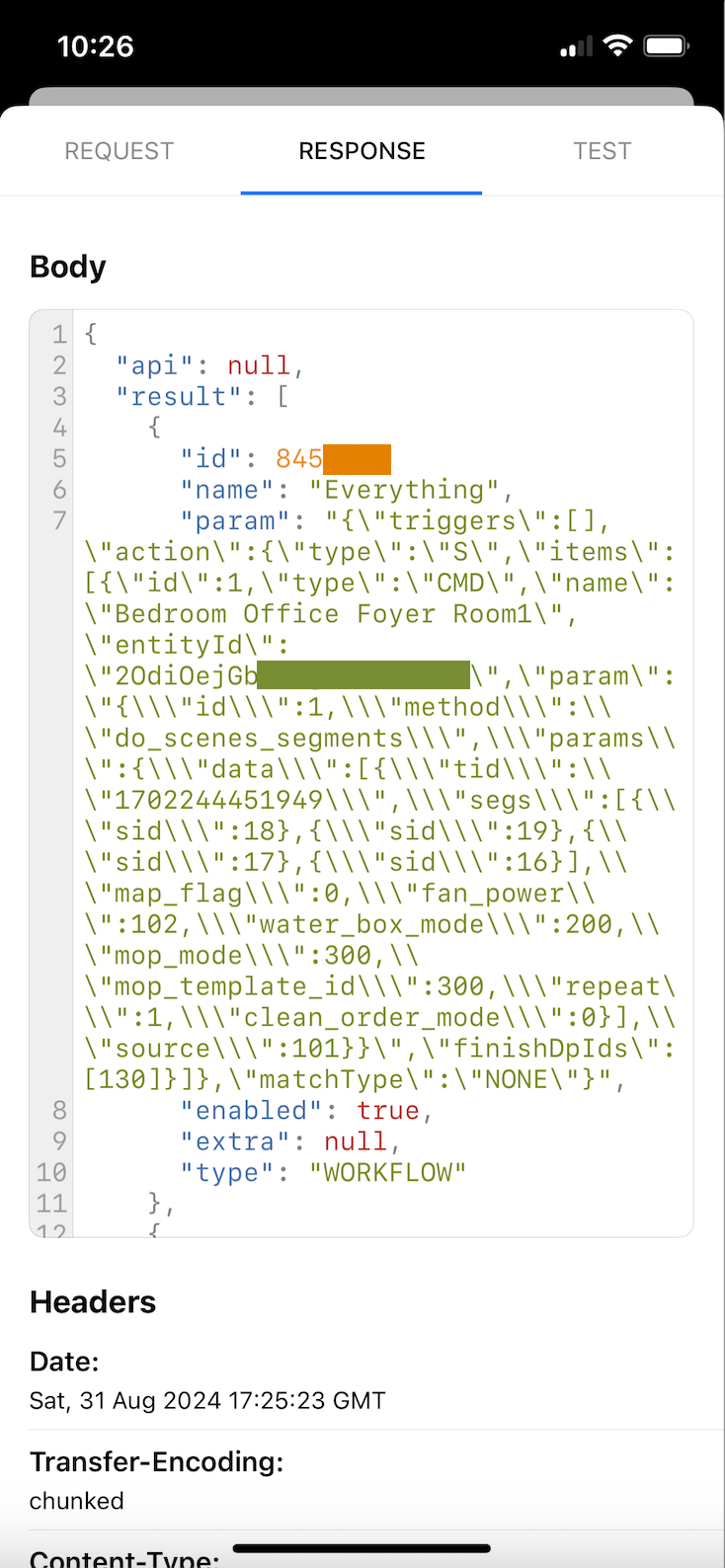
With it recording traffic open the Roborock app, and scroll to the right of your routines to where it says "More". Clicking that will pull up a full list of your routines, and will send a request to the server with the information we need. By jumping back to the WebProxyTool app we can click into the "api-us.roborock.com" folder, and navigate to the https://api-us.roborock.com/user/scene/device/2OdiOejGb... URL, where the device ID matches the one we found earlier. Clicking "Response" will show all of your routines, with the "id" field (for me a six digit code starting 845***) being the "sceneId" we were looking for earlier.
From here we have all of the pieces! Go back to the Shortcuts app and use the Device ID and Scene ID we've extracted with the "Type" of "NormalCommand" to make as many of the routines as you want. Huge thanks to Sashko for his writeup, and hope my version was useful if you're less familiar with Charles.
Richard
Thanks for this, It is really good even for a novice like me. Unfortunately, I think you now have to pay $50 to be able to record the HTTP traffic as no Response option comes up. If you could come up with another free and safe way of doing this it would be much appreciated.
Tobi
Hello Richard. It works perfectly with Proxyman.
Derek
Just tried this, and worked perfectly, despite the comment above from Richard. App has some paid functionality, but worked like a charm for me without that.
Alex (Blog Owner)
Updated! You should just be able to swipe down and ignore the subscription. I went through the flow again and it still works for free, the Response tab was still there.
Marjolein
Hi Alex, Thanks for your manual! I followed all the steps but unfortunately I don’t see a Response tab, only a Request and Test tab. What do I have to do to see this Response tab as well? Kind regards, Marjolein
Jarrod
Incredible. Worked in 8 mins. For me - couple clarities (1) No isOdm needed in Shortcuts (2) Enable “WebProxyTool” is yes/green. Not record HTTPS traffic.
Allen
I just set this up using proxy man. Thanks for the post! I believe the device id isn’t even required to run the routine as I tried running it with only sceneId and it worked. The POST request doesn’t contain the DUID anywhere URL: https://api-us.roborock.com/user/scene/{scene-id}/execute I’m guessing it somehow is able to identify the user through the headers and probably under a user every sceneid is unique even across devices
Allen Ho
I just set this up using proxyman. Thanks for the post! I noticed the DUID isn’t even required for the shortcut to run. Examining the POST request it doesn’t even have device id in the request body, headers or path. URL: https://api-us.roborock.com/user/scene/42624/execute My guess is scene is unique to user and so even if we have multiple devices their scenes will all have different ids, and the user is authed through some header token, thus not needing device id anyhow